How much do your students know about how the web is built and where it travels?
If you’re’ here, you probably know a fair amount already. Now, think about your most confident user at your school. How much do they know about security on the web? Now think about the least confident user on your staff and think how much do they know about security on the web? Now think about your students. How much do they know about security on the web?
If we collated this as a chart or graph, I think you’d see the numbers dwindle severely from you or your head of I.T. all the way down to your new and most infantile of users of the web - your youngest students.
The push I am trying to adopt at my school at the moment is for some kind of awareness of how fragile they are as users of the web and operational security (OpSec) they actually perform on a day-to-day basis. I have tried this in our year 5 and 6 curriculum to some avail and with smaller groups of staff on a similar scale. The snag is, no matter which avenue I take, there is a similar scenario: it’s too difficult to apply to everyday life unless there is obvious incentive. While the complexity isn’t strictly true, it’s that the routines and behaviours people have are so set to cut the shortest path to ‘getting thing’s done’ that going the long way round is a chore.
Year 6 browser lessons and what Firefox extensions do.
Let’s take a year 6 class as the example. There is such a low-level awareness to personal safety and security on the web in general (this is global not just here at my school) that out kids don’t have the maturity of usership to understand that they are extremely vulnerable to password, account breaches and application-led behaviours. This may not be in the immediate future but certainly in the not-to-distant future where they begin to sign up for accounts on the web and apply this basic approach to operational security to every account. They are wide-open to abuse and attack. Apologies for the scaremongering parlance.
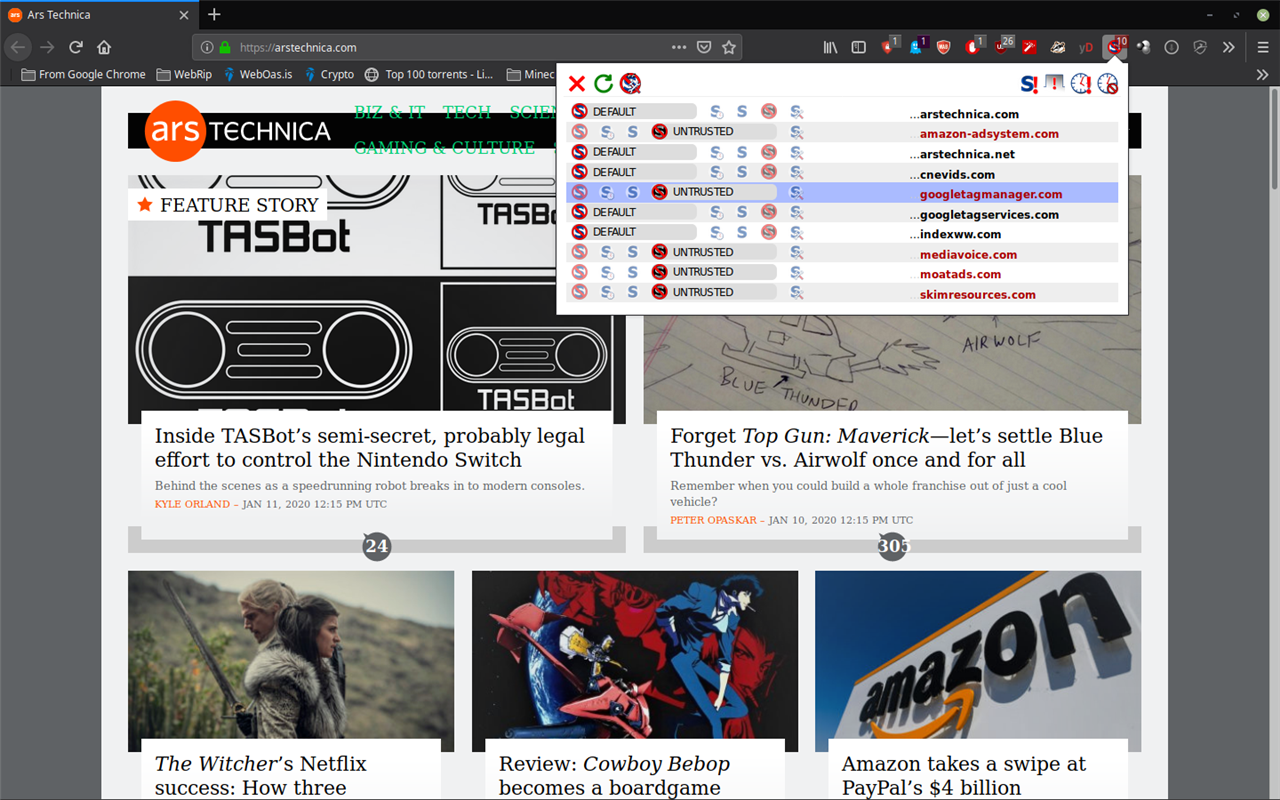
No Script in action on the Arstechnica page in a Year 6 Lesson.
The example in this case of delivery is the test to see how well the students would move away from using Google Chrome to Mozilla Firefox. Then, once there, to use the Firefox extensions such as Ublock Origin and No Script to understand what is on the web but is hidden to everyday user. These hidden aspects are things like cookies and the millions of advertising and data trackers that are embedded into not only web pages, but in some cases, individual pixels.
The overarching issue is the adoption of a new set of behaviours and, as I found out is extremely difficult to change if there is a deep groove in place already. My immediate observation here is that the kids don’t have the awareness of the web and that they, as kids do, follow each other in terms of trends. These trends are usually born from popular models of use sometimes, and not exclusive to, the practices of older siblings and parents.
Why do I come to this observation? Well, I have captive subjects in my house: my son and my wife. My son is currently 6 years old and as with any 6 year old, anything with a screen, a joypad or keyboard is like honey to a bear. The other side of the coin is my wife who is pretty adept at using technology, on the whole, being a graphic designer and digital artist. The issue here, that this is an almost perfect foil, is that she has deeply entrenched sets of behaviours due to the sheer breadth of her daily workflows across a multitude of applications and devices.
We’ll move onto my wife as a use case late and we’ll begin with my son. I thought that he might be too young to understand that the web tracks us and the actions he takes around the web can be tracked and pushed back to him in the form of advertising. Being 6 his spread of use is pretty basic and usually heavily assisted, however his use-case is centred around search and the basic operations of favourite sites he visits - namely YouTube and Minecraft videos from (a favourite of mine too) PixlRiffs. There is also the use of games both on the desktop and iPad.
The easiest part of this was his behaviour and attitude to the computer is such that whatever I tend to say to use he uses. He has no preference being so young and naive he has utmost trust in whatever I suggest. This is both a positive and a reminder that not all households are the same. This also reminds we how blinded the children are at my school in particular are when they adopt new procedures towards connected devices and I observe their actions in IT-based lessons.
The easiest way to show him what was going on was loading up YouTube and looking at the front page to see what is there. What was there? Well, the usual thumbnails of trending topics and the slew of Minecraft videos that are vying for his attention. This is, as I found out, was all I really needed. Because we sat and talked about why the videos were there. Immediately he talked about they are the new ones from PixlRiffs and Mumbo Jumbo and they want him to watch them. So I asked if PixlRiffs and Mumbo Jumbo knew who he was. He gave me that disgusted look that only children can give you when you ask, what in their view is a very stupid question. Of course they don’t know him he exclaimed. Do you know them? Came the reply. Quite.
The next task was to decipher who put the the videos there. Well, them, of course because they produced them. But, why are the thumbnails there trying to get you to click on them. Then we got to the point that YouTube knows we like these channels. So how do they know we like them? Did we tell them? This stumped him until we talked about the control panel in Ublock Origin and No Script. At this point he didn’t know what these things were and what the numbers meant in the extension icons.
The experiment is to roll through the pages on YouTube and watch the numbers increase as the trackers are blocked. This gets to some very high numbers indeed and a perfect example to a 6 year old as we hit 500+ trackers and the idea that there is something we can’t see on the web yet is happening behind the thumbnails finally hits home.
So what are the underlying obstacles in a school setting?
Compartmentalisation with web browsers is a good starting point for increasing your privacy by breaking the cookie links to all web activity in the same browser. Using one browser for one activity splits prevents cookie collaboration.
Google is pretty much the de facto place for search (including YouTube), Docs and access to the web. Why? Well, we are partially to blame. We install Chrome system-wide, set search to Google in managed mode and use Chromebooks across most of the primary school. The children’s trajectory through school until they are independent users (year 6 in our case) is fragmented and peppered with behavioural amplifiers all the way through secondary that line them up perfectly for a fall when they begin to be fully fledged users of networks yet they have little to no understanding of how they work. The other side of this behavioural peppering is that the students have little understanding of why they use their devices in such herd-like ways, that breaking from these deepening traits is nigh on impossible. Just look at shoals of mackerel being eaten by whales - they always go back to being that spiraling mass ready to be eaten once again.
Why is it really hard to break this chain of risky behaviour? Because ergonomically it’s applications are made to be convenient. Convenience, inclusion and price are the central tenets to a popular app. Take the most recent ease-of-use app to make headlines for schools: Zoom. It is a fantastic way to get set up, use, share and group call. It’s also free. Just like Gmail, Instagram, Twitter, TikTok and Facebook are free except you can pay for more options within Zoom. The snag is that there are also serious security flaws in Zoom.
I learned that Zoom had security flaws when I was offered an interview for a very prominent school in Shenzhen and then later backed up by this report. The head of IT at their US office was asking me to install Zoom and use this on a device. I replied back several days later that I was getting errors system-wide at install and from firewall protection that this was not a trustworthy application even though on the face of it (Head of IT and direct download from Zoom’s source) was telling me all was fine. I didn’t get the job based on my alert about this and the request for the use of Skype instead (web-based conferencing wasn’t an option).
Later on that week, I was lambasted from the Director of the school for refusing to install it on my devices even though the position I was applying for was the Head of Technology at their campus. As I say, we are blinded by pre-learned behaviours towards technology, the web due to the need for convenience and cost.
Coming back to the captive audience in my home, I set about wondering if it was possible to change my wife’s behaviour towards her web use and technology on the whole. Bear in mind her job requires convenience as there are more-often-than-not strict deadlines to adhere to in her role. This workflow could not be messed with too much. This included communication apps such as Line (Web and mobile), Gmail, BlueJeans (Adobe) and Zoom for conferencing. These can’t be messed with in too many ways.
What we can pry into here, are the behaviour tracking underbellies in the browser and break those without losing functionality. This couldn’t be a gung-ho attack and would have to be in conjunction with my son’s effort as well as her personal use of the web too. So what would be the similarities and differences be? Well, for son and I we moved all Windows and Mac devices in our house to Linux Mint with the exception of my wife’s Macbook and my Dell as these are for work. Both my son and my wife would begin using Firefox for personal use and my wife would begin compartmentalising her personal and work use into parts of Chrome, Brave, Vivaldi and Firefox.
What is compartmentalism in terms of tech use? It’s where the user, for example, may have a Facebook account and they are heavy users too. This would mean she would now only be allowed to use Facebook in one tab in a single browser and only use it for that purpose. Line in another browser in single tab and so on.
So far this is what she has settled on being helpful, as well as moving all personal correspondence to TutaNota.com and NextCloud for storage - she uses Google Pixel. On her Macbook she uses two logins for work and personal splitting the possibility of a cross divide. For future use we are talking about virtual machines because once they are set up they are very easy to manage.
Her browser use in personal mode is Firefox with these extensions added:
Decentraleyes and
NordVPN on all devices.
While Nord may be not the most progressive and ProtonVPN is a better alternative we know this is the one to watch for future improvements. Also search is now DuckDuckGo with Firefox Focus on the Pixel as a search-only browser.
The upshot to this is that, yes, the convenience factor has gone out of the window and it’s high time to slow the user application down and adopt a more measured approach towards any Internet-connected device ( this includes your assistants, Wi-Fi speakers, health trackers and Ring door bells). Are there more things to think about? Sure, there are things to think about, but these things are how you connect to the internet and how every move you make is being monetised and collated into a huge piece of retail data points from heating your home to monitoring your heart.
And, if you are a teacher of a class of students who are on their way to technological independence on the web, then you have a duty to get on board with this knowledge of how your connections to the internet are not only fraught with attack but are making a model of you. Not sure how this is happening to you, then look at your infinite scrolling and double-taps on Instagram. Look at your daily routines on the web where your behaviour has changed because I bet you give out/ receive star ratings on the food you receive or the holidays you book through Air BnB, Uber, Grab, Food Panda.
It’s time as a teacher of young and inexperienced users of the web, to demonstrate to them that we all should take this a lot more seriously and be somewhat knowledgeable on what the web is actually made of. Moreover, the knowledge that our chemically made up behaviours have changed through likes, emoji, infinite scrolling and the hourly governance of notifications.
Just think, if your Apple watch buzzes and tells you to stand up and you do stand up, then what else can series of apps and connected devices make you do?